Session 1 of the Progressive Terrorism Studies Webinar Series. “The Persistent Online Presence: The Shift in Platform Exploitation Over Time”

How the Salafi-Jihadi movement has been able to exploit the internet to distribute their message has been a key concern of those seeking to challenge these narratives. The first webinar in the Progressive Terrorism Studies Webinar series provided a data-driven update on how the Arabic speaking core of the Salafi-Jihadi information ecosystem has continued to evolve. This is not a new phenomenon – nor restricted to the pop cultural and pseudo-scientific hype regarding al-Dawlat al-Islamiyya – rather, jihadists have been exploiting all means possible on the Internet for decades.
This research comprises over 6.4 million Telegram updates collected in near real-time since June 2017. These updates were collected from channels and groups confirmed to be part of the Salafi-Jihadi movement, stemming from Jihadist exploitation of the internet for over a decade, but focused here on their operation on Telegram. From within this vast archive of material a collection of 4 million instances of URL sharing were recorded for analysis.
The session emphasised the importance of robust design and data collection in the study of Salafi-Jihadi groups.
The subject of study needs to be identified by someone able to:
- recognise the theological references and imagery,
- join online groups by passing the vetting conducted by the Salafi-Jihadi movement in Arabic. If a researcher cannot respond to Q&A in Arabic, it is a sure sign they cannot enter the core of the movement.
Similarly, for analysis which examines change over time the data collection needs to occur in near real-time, as downloading weeks, months, or years after the event does not provide a credible dataset for analysis. This is because the attempted disruption from outside, internal purging of some groups, and the activity of bots, all combine to undermine confidence in time-series analysis of Telegram data collected using a retrospective approach.
The large-scale analysis provides a strategic level overview of the way the Salafi-Jihadi movement has operated since Telegram became its primary platform for communicating with supporters and acting as a core platform for their media output – in combination with other platforms since Europol’s claim of they had removed IS from the internet in November 2019. By examining the URL they share, the analysis shows the breadth of the Salafi-Jihadi presence across platforms and provides an overview into whether there are detectable patterns in their use of different online services.
A reduced version of the domain tool used in the time-series analysis shows the engagement profile of various domains in the study.
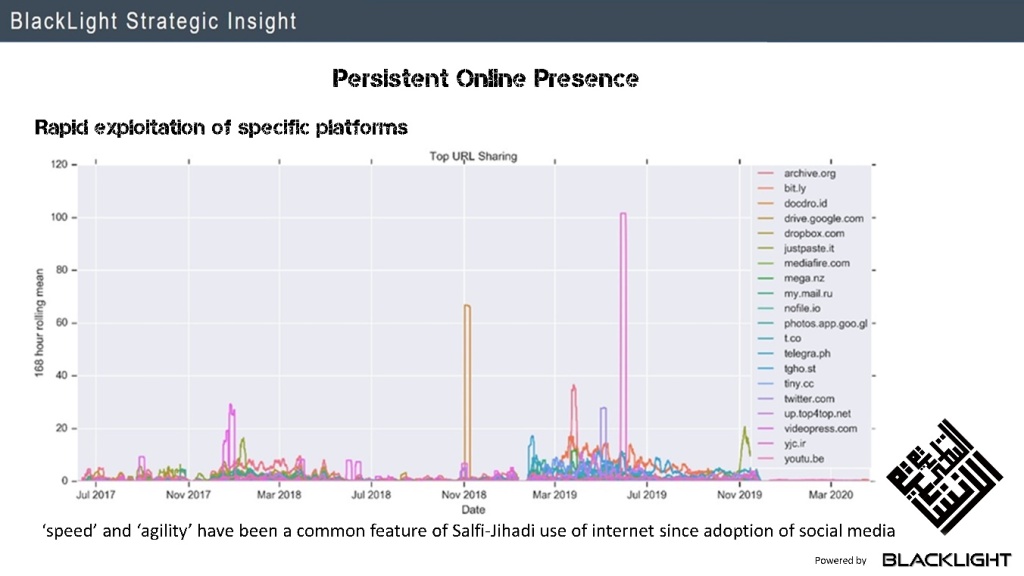
The tool can be viewed here and more detail on the analysis can be found on github.
The analysis showed:
- Some platforms experience persistent engagement profiles, while others experience sudden spikes in use, or short-term exploitation.
- Correlations between the use of different platforms could be used to develop a rapid alert system to locate material.
- Co-citation style network analysis can be used to detect clusters of platforms which are used collectively. This would allow clusters of platforms which are being exploited in a similar way to be supported or work collectively.
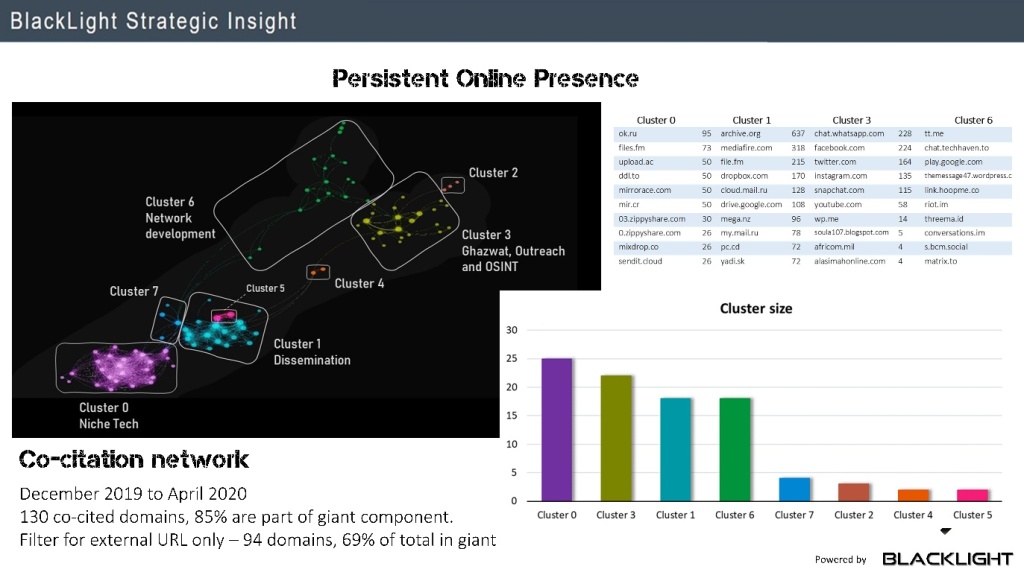
The session built on 2019 the publication by Emily Winterbotham, Dr Ali Fisher and Dr Nico Prucha. This is the largest ever study of traffic between the online platforms that comprise the Jihadi information ecosystem. This study included 24 months of data from the core of the Salafi-Jihadi Telegram network and revealed the inner workings of their multiplatform communication paradigm. The paper demonstrated the different roles that platforms play within the multiplatform information ecosystem, including Telegram, Tamtam, and Matrix.